
Risk Assessment Questionnaire The Institute of Internal Qualys Security Assessment Questionnaire (SAQ) give you the ability to create campaigns to help you send out questionnaires to any number of users and to collect their risk and compliance data.
CANSO Cyber Security and Risk Assessment Guide
Web Application Security Assessment Report cstl.com. Risk Assessment Questionnaire (RAQ) – Summary of Results 3 Introduction The EBA conducts -annual Risk Assessment semi Questionnaires (RAQs) among banks and market analysts.This booklet presents a summary of responses to the RAQs carried out between September and October 2017. 38 banks and 21 market analysts submitted the answers.The RAQ results are published, Application security assessment from Veracode. As a leading provider of application security solutions for companies worldwide, Veracode provides application security assessment solutions that let organizations secure the web and mobile applications and build, buy and assemble, as well as the third-party components they integrate into their environment..
In a world with great risks, security is an ever growing necessity. That’s why there is a need for security risk assessments everywhere. The need for formative assessment is impeccable, as you’d want the assessment to have the best results and help you with your fortifications. Evaluate an application or system’s security controls by utilizing the Application Security Questionnaire (ASQ).
Google Releases Source Code of Security Assessment Questionnaire. Google announced on Monday that it has decided to open source its Vendor Security Assessment Questionnaire (VSAQ) framework to help companies improve their security programs. Self-assessment . This tool allows you to answer the question, "Am I doing enough to secure my system?" At a minimum, use the 20 controls as a benchmark. For higher risk systems, use the detailed control guidance to ensure a robust and thorough analysis of security meaures. Reviews and Audits. We've been told that there is inconsistency in both the security review and internal audit process. This …
Cloud / Hosted / SaaS Security Assessment Page 1 of 25 CLOUD / HOSTED / SaaS ASSESSMENT PURPOSE The purpose of this document is to provide guidance to assess and evaluate the proposed solution’s security and other features and determine key risks. Assessment questionnaires are designed to evaluate one’s strengths and weaknesses. They may also be used to identify and resolve problems that exist in the workplace. One of which would include a risk assessment questionnaire that studies issues that negatively impact an employee’s mental and emotional health.
Security Assurance & Compliance . Email: ciso@miami.edu Phone: 305-243-0281 . Page 4 of 5 . Document Title: IT Security Assessment Questionnaire . Page . 4. of . 5 Support . Will the application require remote access for technical support? Yes No Does the application use an embedded support tool that communicates in/outbound? Yes No Application Security Questionnaire 2.10 Can the application continue normal operation even when security audit capability is non-functional? (For example, if the audit log reaches capacity, the application should continue to operate and should either suspend logging, start …
Self-assessment . This tool allows you to answer the question, "Am I doing enough to secure my system?" At a minimum, use the 20 controls as a benchmark. For higher risk systems, use the detailed control guidance to ensure a robust and thorough analysis of security meaures. Reviews and Audits. We've been told that there is inconsistency in both the security review and internal audit process. This … Information Security Risk Assessment . Start with our risk assessment template, which includes more than 60 common enterprise-wide information security threats. Answer a questionnaire to unlock risk level suggestions. Then customize the risk assessment so it perfectly reflects your organization.
The updated version of the popular Security Risk Assessment (SRA) Tool was released in October 2018 to make it easier to use and apply more broadly to the risks of the confidentiality, integrity, and availability of health information. At Whistic, simplifying third party security risk assessments is our job. That’s why we’ve compiled a list of 5 of the top questionnaires used in IT vendor security assessments today. And the best news? Whistic’s platform supports each and every one of these standardized questionnaires, so you can choose the best assessment for your
Risk Assessment Team Eric Johns, Susan Evans, Terry Wu 2.2 Techniques Used Technique Description Risk assessment questionnaire The assessment team used a customized version of the self-assessment questionnaire in NIST SP-26 “Security Self-Assessment Guide for Information Technology Systems”. This questionnaire assisted the team in Web Application Security Assessment Report Acme Inc Page 3 of 33 COMMERCIAL IN CONFIDENCE Document Authorisation Title Version Reference Author Reviewer Date Web Application Security Assessment Report 1.0 2012-999 RELEASE A N Other D. Boss 1st Sep 2012 Web Application Security Assessment Report
Application Security Assessment Questionnaire 1. Brief outline of the application: it's purpose, intended audience and the types of transactions it perform. 2. What are the development platforms for the application (J2EE/.NET)? What is the development language used ?(Java, C/C++). 3. What are the target operating systems for the application? 4 A vendor risk management questionnaire (also known as a third-party risk assessment questionnaire or vendor risk assessment questionnaire) is designed to help your organization identify potential weaknesses among your third-party vendors and partners that could result in a data breach, data leak or other type of cyber attack.
Risk Assessment Questionnaire (RAQ) – Summary of Results 3 Introduction The EBA conducts -annual Risk Assessment semi Questionnaires (RAQs) among banks and market analysts.This booklet presents a summary of responses to the RAQs carried out between September and October 2017. 38 banks and 21 market analysts submitted the answers.The RAQ results are published This paper is from the SANS Institute Reading Room site. Reposting is not permitted without express Reposting is not permitted without express written permission.
At Whistic, simplifying third party security risk assessments is our job. That’s why we’ve compiled a list of 5 of the top questionnaires used in IT vendor security assessments today. And the best news? Whistic’s platform supports each and every one of these standardized questionnaires, so you can choose the best assessment for your Application risk assessment. Application risk level is determined based on a questionnaire filled out by the application team. This determines the SDL-LOB tasks the application owner must complete and is used to determine if the application is in scope for a security and privacy assessment.
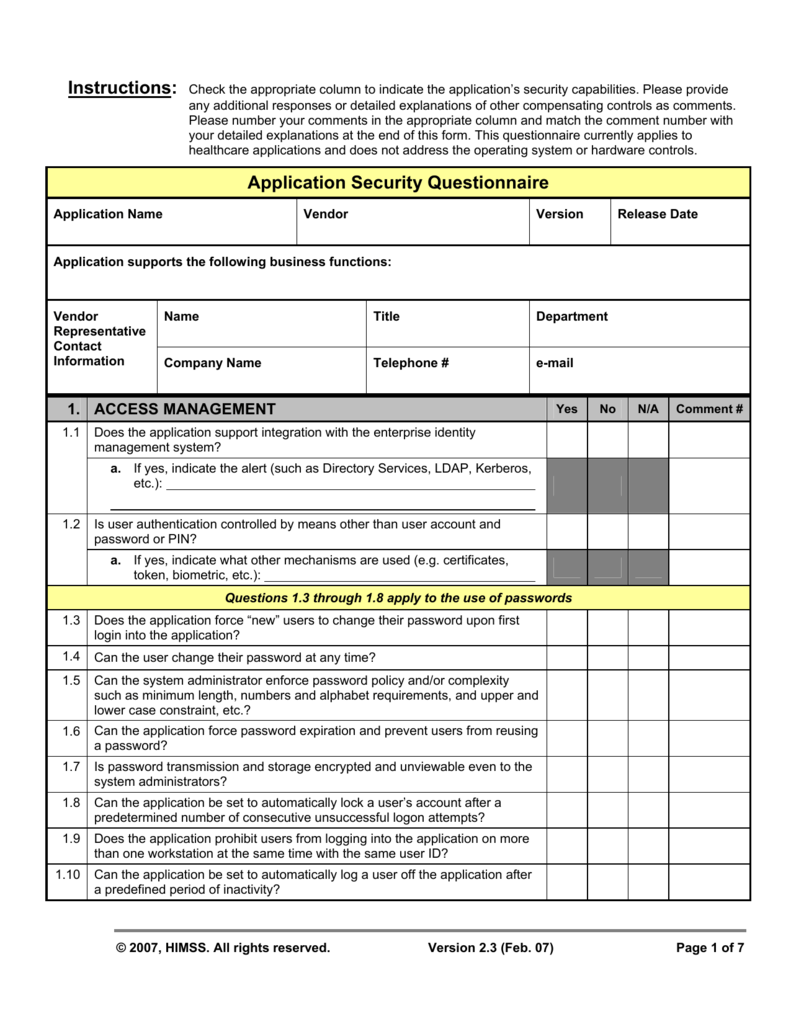
Application Security Questionnaire HIMSS

Risk Assessment Service Risk Assessment Overview. Assessment questionnaires are designed to evaluate one’s strengths and weaknesses. They may also be used to identify and resolve problems that exist in the workplace. One of which would include a risk assessment questionnaire that studies issues that negatively impact an employee’s mental and emotional health., Risk assessment is a term given to the method of identifying and evaluating potential threat, hazard, or risk factors which have the potential to cause harm. Risk assessment questionnaires typically ask questions about risks or risk management to particular respondents..
Cloud Hosted SaaS Assessment Questionnaire. SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements., SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements..
Introduction to Application Risk Rating & Assessment
THIRD-PARTY ASSESSMENT QUESTIONNAIRE. application source libraries Do security specialists conduct technical reviews of ap plication designs? Are security professionals involved in the testing phase of an application? Describe how you protect your applications from covert channels and Trojan code. Halkyn Security Consulting www.halkynconsulting.co.uk [Company Name] Supplier Security Assessment Questionnaire Page 7 of … https://en.wikipedia.org/wiki/Questionnaire At Whistic, simplifying third party security risk assessments is our job. That’s why we’ve compiled a list of 5 of the top questionnaires used in IT vendor security assessments today. And the best news? Whistic’s platform supports each and every one of these standardized questionnaires, so you can choose the best assessment for your.
By failing to properly manage your vendor cybersecurity risk, you could become vulnerable to a breach and the regulatory, reputational and financial consequences that come with it. Venminder provides you with an easy-to-read and comprehensive information security risk assessment for each vendor. Please reload this page with a qpath parameter. E.g.: qpath=questionnaires/ven_template.json Link: Example
Please reload this page with a qpath parameter. E.g.: qpath=questionnaires/ven_template.json Link: Example At Whistic, simplifying third party security risk assessments is our job. That’s why we’ve compiled a list of 5 of the top questionnaires used in IT vendor security assessments today. And the best news? Whistic’s platform supports each and every one of these standardized questionnaires, so you can choose the best assessment for your
VSAQ - Vendor Security Assessment Questionnaires. Web Application Security Questionnaire; Security & Privacy Program Questionnaire; Infrastructure Security Questionnaire Self-assessment . This tool allows you to answer the question, "Am I doing enough to secure my system?" At a minimum, use the 20 controls as a benchmark. For higher risk systems, use the detailed control guidance to ensure a robust and thorough analysis of security meaures. Reviews and Audits. We've been told that there is inconsistency in both the security review and internal audit process. This …
В© SANS Institute 2002, Author retains full rights. Key f ingerprint = AF19 FA 27 2F94 998D FDB5 DE3D F8B5 06 E4 A169 4E 46 THIRD-PARTY ASSESSMENT QUESTIONNAIRE Dec 2015 NOTE: Prior to finalizing business agreements involving confidential data, this completed form should be submitted with Vendor's technical response to Company's Information Security Office (mark a "1" in all boxes applicable for this relationship) Transmit or Access Stores Offsite Risk Data Type
At Whistic, simplifying third party security risk assessments is our job. That’s why we’ve compiled a list of 5 of the top questionnaires used in IT vendor security assessments today. And the best news? Whistic’s platform supports each and every one of these standardized questionnaires, so you can choose the best assessment for your Risk Assessment Team Eric Johns, Susan Evans, Terry Wu 2.2 Techniques Used Technique Description Risk assessment questionnaire The assessment team used a customized version of the self-assessment questionnaire in NIST SP-26 “Security Self-Assessment Guide for Information Technology Systems”. This questionnaire assisted the team in
Evaluate an application or system’s security controls by utilizing the Application Security Questionnaire (ASQ). Cloud / Hosted / SaaS Security Assessment Page 1 of 25 CLOUD / HOSTED / SaaS ASSESSMENT PURPOSE The purpose of this document is to provide guidance to assess and evaluate the proposed solution’s security and other features and determine key risks.
At Whistic, simplifying third party security risk assessments is our job. That’s why we’ve compiled a list of 5 of the top questionnaires used in IT vendor security assessments today. And the best news? Whistic’s platform supports each and every one of these standardized questionnaires, so you can choose the best assessment for your In a world with great risks, security is an ever growing necessity. That’s why there is a need for security risk assessments everywhere. The need for formative assessment is impeccable, as you’d want the assessment to have the best results and help you with your fortifications.
In a world with great risks, security is an ever growing necessity. That’s why there is a need for security risk assessments everywhere. The need for formative assessment is impeccable, as you’d want the assessment to have the best results and help you with your fortifications. VSAQ - Vendor Security Assessment Questionnaires. Web Application Security Questionnaire; Security & Privacy Program Questionnaire; Infrastructure Security Questionnaire
By failing to properly manage your vendor cybersecurity risk, you could become vulnerable to a breach and the regulatory, reputational and financial consequences that come with it. Venminder provides you with an easy-to-read and comprehensive information security risk assessment for each vendor. SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements.
Please reload this page with a qpath parameter. E.g.: qpath=questionnaires/ven_template.json Link: Example Risk assessment is a term given to the method of identifying and evaluating potential threat, hazard, or risk factors which have the potential to cause harm. Risk assessment questionnaires typically ask questions about risks or risk management to particular respondents.

Risk Assessment Team Eric Johns, Susan Evans, Terry Wu 2.2 Techniques Used Technique Description Risk assessment questionnaire The assessment team used a customized version of the self-assessment questionnaire in NIST SP-26 “Security Self-Assessment Guide for Information Technology Systems”. This questionnaire assisted the team in Assessment questionnaires are designed to evaluate one’s strengths and weaknesses. They may also be used to identify and resolve problems that exist in the workplace. One of which would include a risk assessment questionnaire that studies issues that negatively impact an employee’s mental and emotional health.
IT Application Security Questionnaire KnowledgeLeader

DETAILED RISK ASSESSMENT REPORT v2 IT Security & Policy. 17. Has a formal routine Information Security risk management program for risk assessments and risk management. 7. Uses passwords that are a min. of 8 characters, expire at least annually & have complexity requirements. 1. Implements encryption for confidential information being transmitted on external or Internet connections with a strength of, Security best practices. Etc. Application. This is an assessment of the functionality and resilience of the compiled application to known threats. This assessment focuses on the compiled and installed elements of the entire system: how the application components are deployed, communicate or otherwise interact with both the user and server.
Vendor Risk Assessment Questionnaire Template
Application Security Assessment Veracode. In a world with great risks, security is an ever growing necessity. That’s why there is a need for security risk assessments everywhere. The need for formative assessment is impeccable, as you’d want the assessment to have the best results and help you with your fortifications., © SANS Institute 2002, Author retains full rights. Key f ingerprint = AF19 FA 27 2F94 998D FDB5 DE3D F8B5 06 E4 A169 4E 46.
Application Security Assessment Questionnaire 1. Brief outline of the application: it's purpose, intended audience and the types of transactions it perform. 2. What are the development platforms for the application (J2EE/.NET)? What is the development language used ?(Java, C/C++). 3. What are the target operating systems for the application? 4 A more established vendor organization might have a large security team, with different individuals providing information on various topics, e.g. security policy, network security, application security. In a small start-up, each person wears many hats and one person may know enough about what’s going on to complete the entire questionnaire by his or herself.
These risks can be avoided with the implementation of new policies for device usage, device/network management technologies and enhanced skill sets for security administrators and application developers.. The first vital step is a comprehensive risk assessment that details what security … application source libraries Do security specialists conduct technical reviews of ap plication designs? Are security professionals involved in the testing phase of an application? Describe how you protect your applications from covert channels and Trojan code. Halkyn Security Consulting www.halkynconsulting.co.uk [Company Name] Supplier Security Assessment Questionnaire Page 7 of …
SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements. Risk Assessment Service Microsoft has developed a Risk Assessment service to be offered to selected U.S. customers. Our goal is simple: We want to help our customers manage risk in their complex enterprise environments. We have developed a unique approach that will help guide your security strategy to ensure coverage across the infrastructure, application, operations, and organizational
Application Security Questionnaire 2.10 Can the application continue normal operation even when security audit capability is non-functional? (For example, if the audit log reaches capacity, the application should continue to operate and should either suspend logging, start … The applications bearing high risk should undergo a security assessment on a priority basis followed by Medium and Low Risk Applications. Based on the available manpower and resources, issues found during the security assessment should be fixed to improve the security posture of these applications.
Evaluate an application or system’s security controls by utilizing the Application Security Questionnaire (ASQ). A vendor risk management questionnaire (also known as a third-party risk assessment questionnaire or vendor risk assessment questionnaire) is designed to help your organization identify potential weaknesses among your third-party vendors and partners that could result in a data breach, data leak or other type of cyber attack.
SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements. Risk assessment is a term given to the method of identifying and evaluating potential threat, hazard, or risk factors which have the potential to cause harm. Risk assessment questionnaires typically ask questions about risks or risk management to particular respondents.
Risk Assessment Questionnaire Determine Your Security Impact Rating. Introduction. The following questions are designed to help determine the risk rating of line-of-business (LOB) applications. The application team completes this questionnaire to assist in the determination of the risk rating. You can arrange these questions in categories, such Qualys Security Assessment Questionnaire (SAQ) give you the ability to create campaigns to help you send out questionnaires to any number of users and to collect their risk and compliance data.
CANSO Cyber Security and Risk Assessment Guide To help organise efforts for responding to the cyber threat, most relevant international standards suggest applying an approach that divides the ongoing security process into four complementary areas: plan, protect, detect, and respond. See the diagram below. The Plan quadrant includes the creation Risk Assessment Questionnaire Determine Your Security Impact Rating. Introduction. The following questions are designed to help determine the risk rating of line-of-business (LOB) applications. The application team completes this questionnaire to assist in the determination of the risk rating. You can arrange these questions in categories, such
Google Releases Source Code of Security Assessment Questionnaire. Google announced on Monday that it has decided to open source its Vendor Security Assessment Questionnaire (VSAQ) framework to help companies improve their security programs. application source libraries Do security specialists conduct technical reviews of ap plication designs? Are security professionals involved in the testing phase of an application? Describe how you protect your applications from covert channels and Trojan code. Halkyn Security Consulting www.halkynconsulting.co.uk [Company Name] Supplier Security Assessment Questionnaire Page 7 of …
SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements. Please reload this page with a qpath parameter. E.g.: qpath=questionnaires/ven_template.json Link: Example
Instructions Application Security Questionnaire
Application Security Risk Assessment and Modeling. SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements., Information Security Risk Assessment . Start with our risk assessment template, which includes more than 60 common enterprise-wide information security threats. Answer a questionnaire to unlock risk level suggestions. Then customize the risk assessment so it perfectly reflects your organization..
Application Security Questionnaire HIMSS
Instructions Application Security Questionnaire. 09/10/2009В В· The Microsoft Security Assessment Tool (MSAT) is a risk-assessment application designed to provide information and recommendations about best practices for security within an information technology (IT) infrastructure. https://en.wikipedia.org/wiki/Risk_assessment Application risk assessment. Application risk level is determined based on a questionnaire filled out by the application team. This determines the SDL-LOB tasks the application owner must complete and is used to determine if the application is in scope for a security and privacy assessment..
application source libraries Do security specialists conduct technical reviews of ap plication designs? Are security professionals involved in the testing phase of an application? Describe how you protect your applications from covert channels and Trojan code. Halkyn Security Consulting www.halkynconsulting.co.uk [Company Name] Supplier Security Assessment Questionnaire Page 7 of … This paper is from the SANS Institute Reading Room site. Reposting is not permitted without express Reposting is not permitted without express written permission.
В© SANS Institute 2002, Author retains full rights. Key f ingerprint = AF19 FA 27 2F94 998D FDB5 DE3D F8B5 06 E4 A169 4E 46 A vendor risk management questionnaire (also known as a third-party risk assessment questionnaire or vendor risk assessment questionnaire) is designed to help your organization identify potential weaknesses among your third-party vendors and partners that could result in a data breach, data leak or other type of cyber attack.
But remember that risk assessment is not a one-time event. Both your IT environment and the threat landscape are constantly changing, so you need to perform risk assessment on a regular basis. Create a risk assessment policy that codifies your risk assessment methodology and specifies how often the risk assessment process must be repeated Application risk assessment. Application risk level is determined based on a questionnaire filled out by the application team. This determines the SDL-LOB tasks the application owner must complete and is used to determine if the application is in scope for a security and privacy assessment.
WhiteHat Security Index (WSI) gives you an instant, visual overview of the robustness of your website with one score to monitor and manage your overall application security posture. With WSI insights, you can reduce risk, save time, prioritize activities, and improve overall security for your organization. Please reload this page with a qpath parameter. E.g.: qpath=questionnaires/ven_template.json Link: Example
the risk posed by applications is essential to make decisions in security management and thwart attacks. Currently, a generic risk assessment metric is used to assess application security risk (ASR). This does not encompass the basic factors of application security such as compliance, countermeasure efficiency and application priority Security Risk Assessment Questionnaire On-Premise Application Vendor Name Application Name Business Contact Business Architect Purpose & Value NSU FLORIDA ONLY Estimated Start Date: Estimated Go-Live Date: Please ask the vendor to complete the entire questionnaire and submit a copy of their recent SSAE16 report.
application source libraries Do security specialists conduct technical reviews of ap plication designs? Are security professionals involved in the testing phase of an application? Describe how you protect your applications from covert channels and Trojan code. Halkyn Security Consulting www.halkynconsulting.co.uk [Company Name] Supplier Security Assessment Questionnaire Page 7 of … VSAQ - Vendor Security Assessment Questionnaires. Web Application Security Questionnaire; Security & Privacy Program Questionnaire; Infrastructure Security Questionnaire
В© SANS Institute 2002, Author retains full rights. Key f ingerprint = AF19 FA 27 2F94 998D FDB5 DE3D F8B5 06 E4 A169 4E 46 Risk Assessment Service Microsoft has developed a Risk Assessment service to be offered to selected U.S. customers. Our goal is simple: We want to help our customers manage risk in their complex enterprise environments. We have developed a unique approach that will help guide your security strategy to ensure coverage across the infrastructure, application, operations, and organizational
Security Assurance & Compliance . Email: ciso@miami.edu Phone: 305-243-0281 . Page 4 of 5 . Document Title: IT Security Assessment Questionnaire . Page . 4. of . 5 Support . Will the application require remote access for technical support? Yes No Does the application use an embedded support tool that communicates in/outbound? Yes No 17. Has a formal routine Information Security risk management program for risk assessments and risk management. 7. Uses passwords that are a min. of 8 characters, expire at least annually & have complexity requirements. 1. Implements encryption for confidential information being transmitted on external or Internet connections with a strength of
Application security assessment from Veracode. As a leading provider of application security solutions for companies worldwide, Veracode provides application security assessment solutions that let organizations secure the web and mobile applications and build, buy and assemble, as well as the third-party components they integrate into their environment. Risk Assessment Questionnaire (RAQ) – Summary of Results 3 Introduction The EBA conducts -annual Risk Assessment semi Questionnaires (RAQs) among banks and market analysts.This booklet presents a summary of responses to the RAQs carried out between September and October 2017. 38 banks and 21 market analysts submitted the answers.The RAQ results are published
Google Releases Source Code of Security Assessment Questionnaire. Google announced on Monday that it has decided to open source its Vendor Security Assessment Questionnaire (VSAQ) framework to help companies improve their security programs. SAQ streamlines your third-party and internal risk assessment processes right from the questionnaire creation phase. With SAQ, you easily design in-depth surveys to make business-process control assessments of security policies and practices of third parties and internal staff, and their compliance with industry standards, regulations and internal requirements.
Security best practices. Etc. Application. This is an assessment of the functionality and resilience of the compiled application to known threats. This assessment focuses on the compiled and installed elements of the entire system: how the application components are deployed, communicate or otherwise interact with both the user and server Evaluate an application or system’s security controls by utilizing the Application Security Questionnaire (ASQ).


